Any financial institution that collects personally identifying information ("PII") is subject to the Gramm Leach Bliley Act ("GLBA"). Compliance is mandatory and there must be a policy in place to protect the information from foreseeable threats in data security and integrity. All companies significantly engaged in activities that are financial in nature are subject to GLBA as well. Businesses should be concerned with two topics arising from the GLBA. One is "Privacy" or "Information Privacy." The other is "Information Safeguards" or the "Safeguards Rule". This program includes policies, references and training to help you understand and put forth good faith compliance against this important regulation.
Implementation Steps in this Guide
-
Review, Edit and Distribute the GLBA Information Privacy, Safeguards and Security Policy
-
Review and Edit the Responding to Information Compromise Guideline
-
Allow Employees to Start the Information Compromise Report Form
Review, Edit and Distribute the GLBA Information Privacy, Safeguards and Security Policy
The mandate requires you to create a policy for employees to understand and follow the procedures established in your Red Flag Program. Compli provides a starting point for this policy. Find the Identity Theft Red Flag Policy for Employees and follow the instructions inside. Much of the information you need to put in this policy can be taken directly from the Red Flag Program.
Review and edit the policy
- Click on the Library tab
- Search for "GLBA Information Privacy, Safeguards and Security Policy" and click on it
- Click on the Edit button to view the list of versions
- Click Create Draft to the right of the latest published version
- Click Edit next to the Draft version that you just created
- Make desired changes to the policy
- Click Publish to finish editing the policy
Schedule the activity for distribution
- Click on the Workspaces tab
- Click on the Consumer Finance workspace
- Click on the Privacy initiative
- Click on the GLBA Information Privacy, Safeguards and Security Policy
- Click on Groups and assign to the appropriate groups, such as All Employees
- Click on Schedule and set an annual schedule based on the Hire Date.
- Click Save
Review and Edit the Responding to Information Compromise Guideline
- Click on the Library tab
- Search for "Responding to Information Compromise" and click on it
- Click on the Edit button to view the list of versions
- Click Create Draft to the right of the latest published version
- Click Edit next to the Draft version that you just created
- Make desired changes to the guideline
- Click Publish to finish editing the guideline
- Click Permissions and assign to the appropriate group(s), such as All Employees
Distribute the GLBA Privacy and Safeguards Training
| Title | Duration (Minutes) | Type | Description |
| GLBA Privacy and Safeguards Training | 15 | Course | This course is about the legal requirements for protecting customer information. Upon completion of this course, you will be able to: - Understand the legal requirements for protecting customer information - Recognize what your obligations are to protect their personal information - How to dispose of personal information |
Schedule the activity for distribution
- Click on the Workspaces tab
- Click on the Consumer Finance workspace
- Click on the Privacy initiative
- Click on GLBA Privacy and Safeguards Training
- Click on Groups and assign to the appropriate groups, such as All Employees
- Click on Schedule and set an annual schedule based on the Hire Date
- Click Save
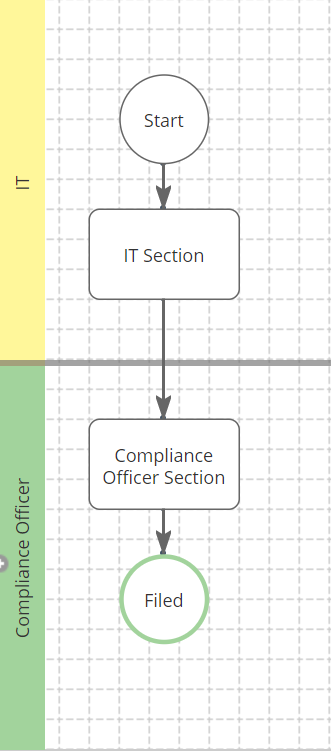
Schedule the Safeguards Monitoring Report Form
Use this form to document an employee’s knowledge of the safeguards for which they are responsible or for the area in which they are working during the relevant reporting period. The information provided will help gain a better understanding of the safeguards in place throughout the organization and will help in efforts to continually monitor and improve safeguards related to customer information.
Review the Process Workflow
Set the form routing
- Click on the Admin tab
- Click on Workflow/Forms subtab
- Click on Processes
- Search for and click on Safeguards Monitoring Report Form
- Edit the routing rules for each stage by following these suggestions:
Stage Suggested Routing Rule Description IT Section Subject or Queue Route to the "Subject" (i.e. the person to whom the system sent this form). This stage can alternatively be assigned to a queue. Compliance Officer Section Queue Route to the Compliance Officer Queue, or equivalent.
Schedule the Activity for distribution
- Click on the Workspaces tab
- Click on the Consumer Finance workspace
- Click on the Privacy initiative
- Click on the Safeguards Monitoring Report Form
- Click on Groups and assign to the appropriate group(s), such as your IT Director or Privacy Coordinator
- Click on Schedule and set the appropriate schedule. We suggest a quarterly schedule. Be sure to add a number of days to distribute the form before it is due.
- Click Save
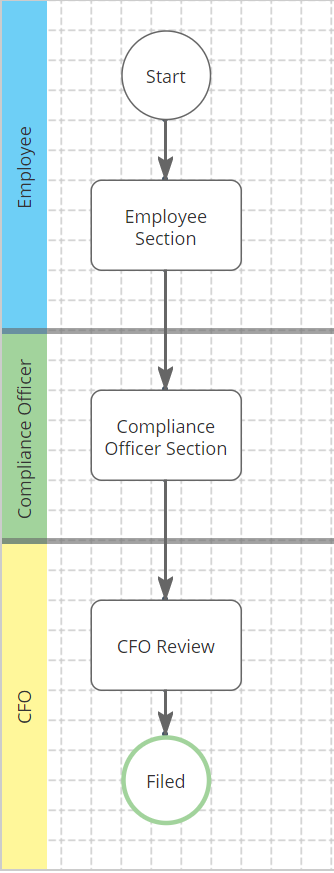
Allow Employees to Start the Information Compromise Report Form
Use this form so the Company can follow through with an investigation and response if an employee knows, or suspects, that private customer information has been stolen or compromised.
Review the Process Workflow
Set the form routing
- Click on the Admin tab
- Click on Workflow/Forms subtab
- Click on Processes
- Search for and click on Information Compromise Report Form
- Edit the routing rules for each stage by following these suggestions:
Stage Suggested Routing Rule Description Employee Section Subject Route to the "Subject" (i.e. the person who started the form) Compliance Officer Section Queue Route to the Compliance Officer Queue, or equivalent. CFO Review Queue or Supervisory Level Route either to a queue that contains your CFO or up the hierarchy to the CFO if that person is in the management hierarchy.
Set the Activity to be startable by All Employees
- Click on the Workspaces tab
- Click on the Consumer Finance workspace
- Click on the Red Flags initiative
- Click on the Information Compromise Report Form
- Click Edit and set the Start Menu Folder to "Report an Incident" or something similar
- Click Groups and assign "All Employees" (or another set of group as appropriate) within the "In Start Menu" for section.
- Click Save
Review the related Information Security Initiative
The best defense against the constantly evolving threat of cyber criminals is an Information Security initiative as part of your workforce compliance program. Your employees provide the best security, or greatest vulnerability, for the private data you are responsible for safeguarding. Every member of your workforce needs to be aligned on the goals of maintaining privacy standards and protocols to protect private information. See the Information Security initiative to learn more.
Comments
0 comments
Please sign in to leave a comment.